Cybercriminals are on the prowl: practically every month, we hear of another cyberattack, often unfortunately successful. The eCommerce industry is one of hackers’ favorite targets alongside the financial sector due to the nature of the data processed. Personal data handled by companies in this sector can fetch a high price on the black market, and the countless payment transactions in eCommerce are ideal for fraud.
It’s no wonder that companies are investing more and more in mobile commerce app security measures. A good backup is, of course, essential, but implementing best practices can minimize the risk of a successful cyberattack to almost zero. The principle of “prevention is better than cure” definitely applies here.
Many eCommerce companies sell both through online stores and mobile apps. The latter are becoming increasingly popular with shoppers, which means they also attract cybercriminals as easy targets. Their specific nature requires a slightly different approach to mobile commerce security.
In our article, we suggest best practices in designing, implementing, and maintaining apps that help reduce risk to a minimum. Hint – it’s not just about technicalities, but largely about educating users. Fight the vulnerabilities with our tips and access the benefits of mobile commerce without risk.
Mobile Commerce App Security vs. Web Security: How Do the Approaches Differ?
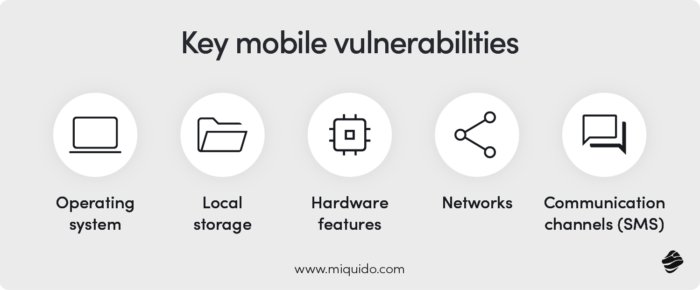
Since mobile devices have numerous sensors and permissions, cybercriminals often target their operating system, hardware, and local storage instead of server-side vulnerabilities and client-side scripts.
Mobile devices frequently connect to different networks, increasing susceptibility to network-based attacks. This tendency is reducing with the expansion of fast and cheap mobile transfer but still exists. On the contrary, web apps are often targeted through DNS spoofing and similar techniques.
Rogue Apps – a Major Mobile Commerce Security Threat
Malicious software often spreads through rogue apps that can closely resemble original applications. Although app stores are implementing more security measures, this problem is hard to avoid. According to research by Avast conducted in 2018, more than half of users couldn’t distinguish between real and fake apps. Despite user awareness of cyber threats growing significantly over the past five years, copycats still pose a valid risk.
WhatsApp’s case can be a good example of how quickly danger can spread even in the case of the most recognized and used mobile apps. In 2021, the Pink Theme Scam affected numerous users, stealing their personal information. It was designed as a fake update campaign with a new color theme for WhatsApp, with the malware spreading via phishing messages containing an install link.
App Store Attacks – Issue with Heavy Impact on Mobile Commerce
Another problem is attacks on app stores. For example, in 2023, cybercriminals exploited a critical vulnerability in Samsung’s Galaxy Store. As a result, thousands of malicious apps were installed on users’ devices without their consent.
In 2021, multiple apps infected with the Joker malware were found on the Google Play Store. This malware was designed to subscribe users to premium services without their consent, leading to significant financial losses. The Joker malware targeted thousands of users before being removed from the store.
Native vs. Cross-Platform: Mobile Commerce Security Considerations
Does it really matter whether your mobile app is native or cross-platform? A strong point of native development is the ability to achieve deeper integration with platform-specific security features and updates. On the other hand, it’s not such a huge difference. Thoughtful development of cross-platform apps, considering robust security practices and regular updates, can also be highly secure.
Common Security Threats in Mobile Commerce
Similar to online stores and web applications, mobile apps have many vulnerabilities. Some threats can spread much faster and on a larger scale in their case.
This is true for malware, which can be easily implemented via app stores, as confirmed by the aforementioned Joker example. How can you protect yourself against such a threat? Primarily through constant monitoring. Much, however, lies in the hands of the app store provider, who controls the flow of applications on their platform.
Phishing and its mobile-specific variant, smishing, are also significant threats to mobile apps. Cybercriminals use SMS to send messages posing as an eCommerce company to trick users into installing malicious software or stealing sensitive information.
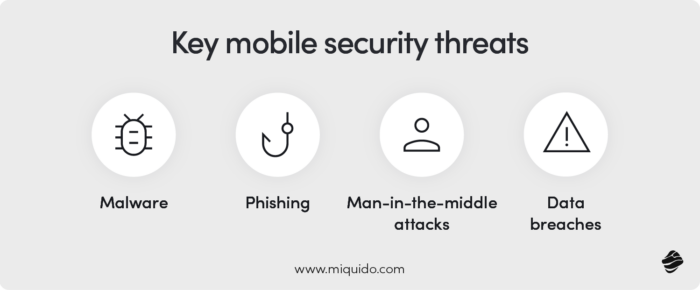
Man-in-the-middle (MitM) attacks are another risk linked to mobile apps. These attacks exploit network vulnerabilities to intercept and potentially alter communication between two parties without their knowledge. In the case of mobile apps, cybercriminals usually access the smartphone through a rogue access point that mimics legitimate Wi-Fi networks. It could even have a familiar name to the one the user usually connects to. Once they connect to the fake network, the attacker can intercept their data.
Although we usually associate the cyberattacks with the external hackers and organized groups, sometimes they are carried out by the insiders. That was the case of 2020 Shopify data breach, when transactional records of approx. 200 merchants were accessed by two rouge employees. In eCommerce, employees often have direct access to sensitive information, which makes this type of risk more elevated than in other industries.
Data Breaches in Mobile Apps – Why Do They Happen and What Can They Result In?
Due to the use of local storage, mobile apps can become a channel for data breaches where sensitive information like passwords and credit card numbers leaks. This can happen due to various reasons related to the app’s architecture, encryption, insecure APIs, among others.
Even the biggest players on the market are affected by such data leaks. WhatsApp experienced a significant one in 2023, with 500 million users’ data affected. In the case of Honda’s commerce platform, the 2023 password reset hack was hiding in a flawed API.
Vulnerabilities can hide in the code of the eCommerce platforms companies hold their shops on. That was the case with Magento 1.x, which experienced the injection of malicious scripts a few years ago, affecting over 2000 shops, including Tupperware.
Good Practices for Mobile Commerce App Security
Although you cannot predict all scenarios, the mobile commerce app security largely depends on you. Of course, a lot of responsibility also lies with users – their decisions and behaviors can open the door to hackers. However, by choosing the right preventive measures and best practices in designing and maintaining software, you can make their task as difficult as possible.
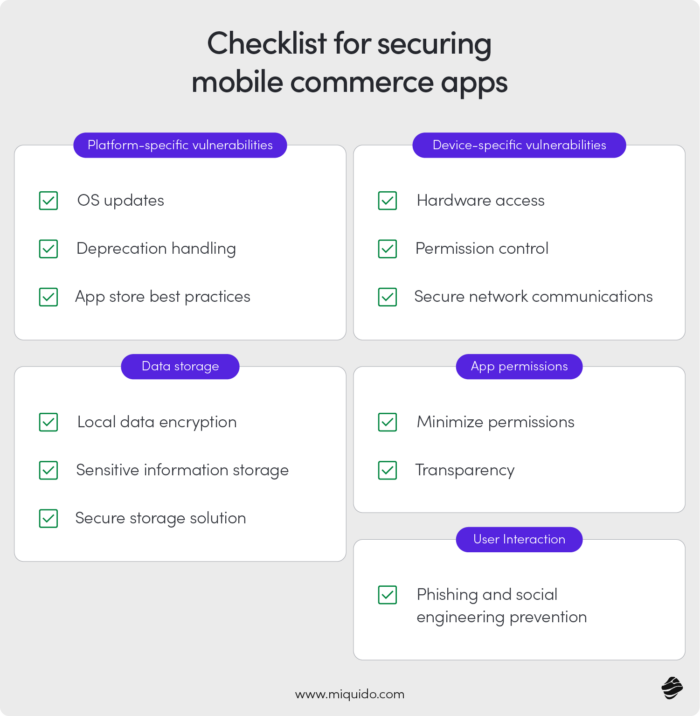
What should you keep in mind? Our tips are divided based on the types of vulnerabilities characteristic of mobile apps. Here’s your ultimate checklist.
Platform-Specific Vulnerabilities
Keep Operating Systems Updated
- Ensure your app supports the latest OS versions and encourage users to update their devices regularly. This minimizes the risk from OS vulnerabilities affecting your app.
- Implement mechanisms to gracefully handle and notify users about deprecated OS versions.
Leverage App Store Security Best Practices
- Adhere strictly to app store guidelines and leverage any available mobile commerce app security tools and services provided by the app stores.
- Regularly monitor for any reported malicious apps that may mimic or interact with your app and report them to the app store.
Device-Specific Vulnerabilities
Secure Hardware Access
- Limit access to hardware features (e.g., GPS, camera, microphone) only to those functionalities that are essential for your app.
- Implement fine-grained control over hardware permissions and regularly audit these permissions.
Ensure Secure Network Communications
- Enforce the use of secure communication protocols (e.g., HTTPS) to protect data transmitted over networks.
- Educate users about the dangers of using unsecured public Wi-Fi networks and consider implementing additional mobile commerce security checks when such networks are detected.
Data Storage
Encrypt Local Data Storage
- Always use strong encryption to protect any data stored locally on the device.
- Avoid storing sensitive information locally if possible. Instead, use secure backend systems to store and manage sensitive data.
Protect Sensitive Information
Implement secure storage solutions for sensitive data such as tokens or credentials, using encrypted keychains or secure storage APIs. Regularly audit your app’s data storage practices and ensure sensitive data is never stored in plain text.
App Permissions
Minimize App Permissions
- Adopt the principle of least privilege by requesting only the permissions absolutely necessary for your app’s functionality.
- Implement transparent permission request dialogs explaining why each permission is needed, encouraging users to scrutinize and make informed decisions.
User Interaction
Mitigate Phishing and Social Engineering Risks
- Educate users about the risks of SMS phishing (smishing) and app-based social engineering attacks. Implement in-app mechanisms to verify the legitimacy of communications and provide clear guidance on how to recognize and report suspicious activity.
Strong Encryption for Mobile Apps – Which Solution to Choose?
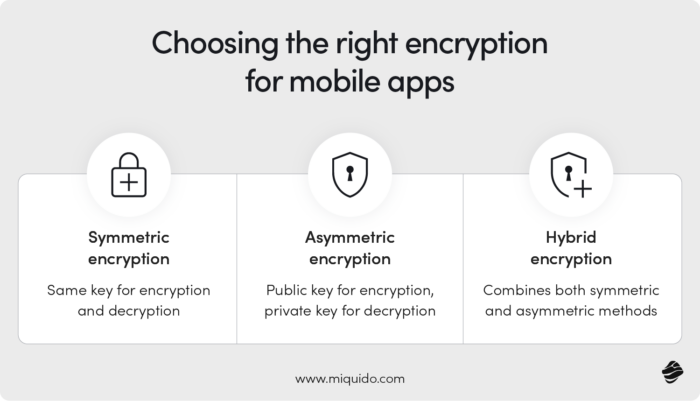
Encryption is an excellent shield against cybercriminals, but you must know which solution suits your needs best. Encryption methods divide into symmetric (those that use the same key for both encryption and decryption) and asymmetric ones (using a pair of keys – public key for encryption and private key for decryption). You can also combine both methods using hybrid encryption.
Among symmetric encryption methods, AES (Advanced Encryption Standard) stands out as the most widely used due to its strength and speed. With key lengths of 128, 192, and 256 bits, it is popular in eCommerce and high-risk organizations, proving its credibility (the USA government uses this encryption method). The 256-bit version is considered nearly unbreakable with current technology.
For mobile apps, AES is a perfect solution due to its efficiency and speed – a feature crucial for mobile devices which often have limited processing power and battery life. Also, AES is natively supported by mobile operating systems (iOS, Android) and easily integrated into mobile commerce applications.
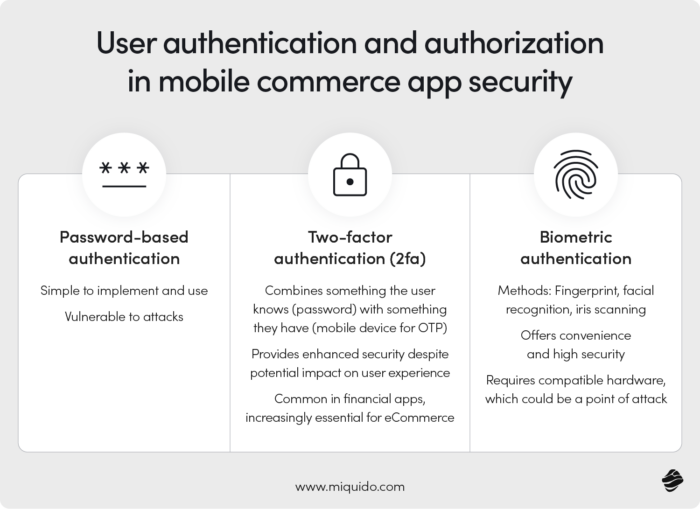
User Authentication and Authorization
Cybercriminals often target the moment of logging into the mobile app or performing a crucial action that requires authorization as a gateway to user data. Strong authentication methods can prevent them. Instead of password-based authentication, which is simple to implement and use but susceptible to attacks, consider using 2FA. Relying solely on passwords exposes your app to poor user password practices, whereas implementing a stronger method allows you to take control of security.
Two-factor authentication (2FA) combines two different methods of authentication, typically something the user knows (password) and something the user has (a mobile device for OTP). Although it may negatively affect user experience, it is worth the safety it provides. In financial apps, 2FA is already common, and considering the rise of cybercrime, it may soon also become an essential element of the eCommerce experience.
If these two methods don’t suit you, consider biometric authentication. Whether it’s fingerprint recognition, facial recognition, or iris scanning, it is convenient and fast, and its security level surpasses others. However, it requires compatible hardware, which could also become a point of attack.
Implement the best mobile commerce security practices in your app
In order to provide mobile app security, you need to, first of all, stay alert. The cyberattacks landscape is changing all the time – new, often more sophisticated methods are appearing, and others fade. Remaining flexible and constantly adapting your development and maintenance methods is the key to staying secure.
As a company specialized in custom eCommerce software development (with special emphasis on mobile commerce app development services), we can help you achieve that goal.




![[header] 29 top ecommerce app features you need to know](https://www.miquido.com/wp-content/uploads/2024/02/header-29-top-ecommerce-app-features-you-need-to-know-432x288.jpg)




