One harsh reality is that mobile banking security issues will never end.
The reason is pretty simple. More and more banking transactions are taking place online, and bad actors will always look for vulnerabilities to exploit. For example, between 2022 and 2023, mobile fraud attacks increased from 47% to 61%.
But here’s the silver lining: you can prevent most of these attacks if you take your mobile banking app security really seriously.
How, you ask? Well, this article is a good start for you. We will cover everything you need to know about mobile banking apps security, including how to secure your mobile banking app.
But let’s start with the basics.
Introduction to Mobile Banking App Security
On average, 80% of mobile banking users have security-related concerns:
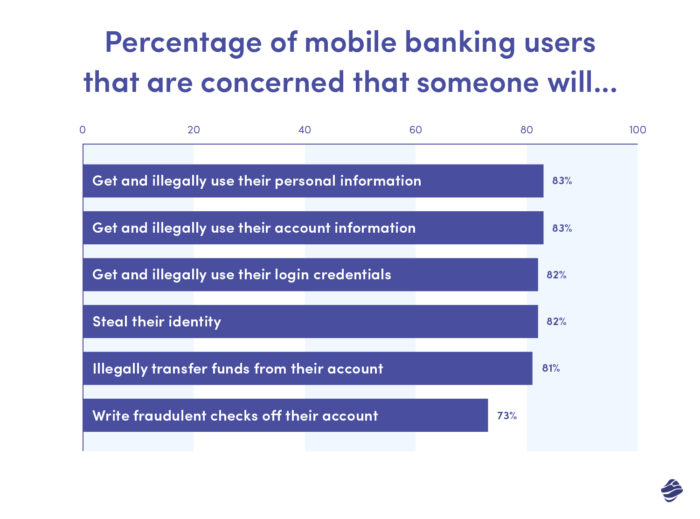
This means that banking and fintech companies entering the mobile banking app market have a lot of work to do to gain their user’s trust.
But that’s not even the reason why security is so important. Security breaches can also be very resource-intensive. You may have to spend lots of time and money on incident investigation, remediation, regulatory fines, and even legal fees. These expenses can run into millions of dollars, not to mention the reputational damage.
For instance, we all saw Capital One pay an $80 million fine following a data breach in 2019. These costs can seriously affect your profitability.
Common Mobile Banking App Security Threats
Before proceeding, let’s get familiar with some of the most common mobile banking attacks.
- Hacking: Hackers constantly look for security vulnerabilities in your app’s code or users’ activities to gain unauthorized access. For instance, if your app lacks proper encryption, they might sneak in through insecure connections like public Wi-Fi networks, i.e., man-in-the-middle attacks.
If successful, they can directly tweak your code to perform unwanted transactions or compromise your customers’ data.
- Data breaches: A data breach occurs when bad actors access sensitive customer data illegally. This data could include their transaction history, PIN, and social security number.
Cybercriminals may proceed to use the data for further financial fraud, such as taking a loan on the customers’ behalf. They can also sell the data in the black market.
Don’t assume hacking your app is the only way to commit a data breach. Unpatched loopholes in third-party integrations can also be a culprit. For instance, Flagstar Bank suffered a data breach because of the vulnerability in MoveIt, the solution they use for file transfers.
- Fraud: The final threat is fraud. We’ve mentioned one way this can happen, i.e., through customer data. But there are other ways, too.
For instance, bad actors can make fake banking apps that mimic yours. Users can download these versions on their mobile devices and unknowingly insert their login details. This opens the door for account takeovers.
Best Practices in Mobile Banking Apps Security
Let’s now examine how to secure mobile banking apps from different kinds of security threats.
1. Follow Secure Coding Practices
Your app’s foundation must be solid for the application to be secure. Code is the foundation of your mobile banking app.
By maintaining secure coding practices in your FinTech app development process, you’ll minimize vulnerabilities in your code and make your app resilient to attacks.
There are multiple widely recognized secure coding standards for your perusal. For instance, check out the OWASP (Open Web Application Security Project) standard below. It features various ways to ensure that your code is secure, from input validation to authentication and session management:

Other organizations like NIST (National Institute of Standards and Technology) and ISO (International Organization for Standardization) also have guidelines for secure coding. You can even combine more than one standard for a well-rounded approach.
2. Focus on Data Encryption
Data encryption involves using cryptographic algorithms to convert readable data into unreadable form. Assume a hacker gains access to user credentials. They’ll be unable to make sense of it without the decryption key.
Always opt for recognized encryption standards, such as AES and RSA, for the best results. You should also keep your decryption key secure, advisably, through top key management solutions like Azure Key Vault or Oracle Cloud Infrastructure Vault.
3. Perform Regular Audits
Security threats evolve. So, even the most secure code can develop some hidden weaknesses. Regular audits help you quickly identify and address these flaws before they hurt your app.
Ideally, you should perform these audits biannually. But it’s even better if it can be more frequent, say quarterly. You should also do it after every major code change or update.
4. Use Authentication and Authorization
Authentication and authorization are two crucial security must-haves for every mobile banking app.
Authentication involves confirming your user’s identity before granting them access to the app. This prevents unwanted access.
Authentication often requires a password. However, this authentication method has proven to be less secure. That’s why you should pair password authentication with other verification methods to create multi-factor authentication.
For instance, you can use password authentication alongside biometric authentication methods (like face identification) or one-time password confirmation. So, let’s assume someone who knows a user’s login credentials tries logging into their account. They’ll still be unable to use the app because of the extra layer of security.
Now, let’s talk about authorization. Authorization involves deciding what users can do with your app. Ideally, you should follow the least privilege principle when implementing authorization. This means granting just the minimum permission necessary for a user to perform their roles.
For example, you want to limit your end user’s access to sensitive data, like your code’s backend. Similarly, your customer support agents shouldn’t have access to initiate transfers from users’ financial accounts.
5. Leverage Machine Learning (ML) for Fraud Detection
Machine learning can be valuable to your mobile banking app security arsenal. A study showed that ML promises up to 96% accuracy in predicting fraudulent transactions.
Here’s how the magic happens:
First, you have to train the ML algorithm with lots of datasets. This includes historical transactions, both fraudulent and legitimate ones. From this, they can learn to identify anomalies and patterns that could indicate malicious activity.
After training your model, it can now help you analyze every transaction in real time. By doing this, it can identify patterns that indicate there’s fraudulent activity going on. For instance, a transaction that doesn’t align with the user’s usual spending trend. Then, it automatically notifies you and the user of this suspicious activity.
This is just a high-level overview of how this system works. Check out our guide on machine learning for fraud detection for a better understanding.
6. Follow Regulatory Standards
Financial and data regulatory standards feature very strict guidelines for collecting, securing, and using customers’ data. Playing by these rules will help you minimize the chances of security issues occurring.
Moreover, non-compliance can attract hefty fines. For instance, let’s say your bank app operates in the EU or serves EU mobile banking customers. Failure to comply with GDPR might attract fines of up to 20 million euros or 4% of your annual revenue. Plus, there’s the headache of legal battles.
So, take time to research the data regulatory standards that apply to your operating jurisdictions and follow them strictly. For example, if your mobile bank customers are in the EU, you want to prioritize standards like GDPR and PSD2.
7. Prioritize User Education and Awareness
Not all successful cyber threats are on the development team. Users play an important part, too. For instance, users can give bad actors a free pass when they fail to protect their passwords. You can only minimize these user-side vulnerabilities by educating your online banking users.
Essentially, you should inform them about the tactics cybercriminals use to gain access to user accounts and how to avoid them.
You can raise awareness via different channels like email and app notifications.
Emerging Trends in Mobile Banking App Security
Cybercriminals are constantly coming up with new ways of attacking banking apps. You must stay abreast of emerging trends in digital banking security if you don’t want to play catch up. So here are some trends you need to explore:
AI-driven Security Measures
Apart from fraud detection, AI can also help with adaptive authentication. It can learn user behaviors and tweak authentication requirements accordingly.
For instance, if a user logs in from an unusual location or attempts a high-value transfer, the system might ask for extra verification. But for routine activities, it can maintain passwords. This helps you maintain security without sacrificing the user experience.
Quantum Resistant Cryptography
The use of quantum computers will become widespread soon. These computers can use special algorithms to crack most of the top encryption standards we have today. For instance, Shor’s algorithms can break RSA encryption.
That’s why quantum-resistant cryptography (QRC) is fast becoming a vital security trend. With quantum-resistant algorithms like Kyber and Classic McEliece, you can future-proof your app against threats from quantum computers.
Blockchain
Blockchain can help improve security in multiple ways, especially for transactions and data storage.
The technology can offer enhanced security features for transactions and data storage, particularly through cryptography and decentralization. However, it’s not inherently tamper-proof and has its own vulnerabilities.
Evaluate its specific use case and security requirements before implementing blockchain solutions.
Mobile Banking Apps Security Case Studies
Having examined how to secure mobile banking app, let’s see how we’ve helped some financial institutions nail their security game.
Nextbank
In 2020, NextBank needed a revamped mobile banking application to expand its offerings. To achieve this, they needed a partner that could balance innovative mobile banking app features with scalability and security. They came to us, and we helped them:
- Implement robust data encryption and multi-factor authentication features
- Follow OWASP security standards
- Conduct penetration testing and external audits
The result? Nextbank runs regular external audits like application security testing and penetration testing. These tests have consistently confirmed the app’s compliance with relevant security standards.
BNP Paribas’ GOMobile
BNP Paribas wanted a more intuitive mobile banking experience for their mobile users. For that, they needed to redesign their mobile channels completely. They knew security was a key factor in this project. We partnered with them for this project.
With the help of other security solutions like Autenti and IDENTT, we helped BNP Paribas with:
- Reliable authentication solutions
- Digital identity verifications
- Early detection and tackling of potential vulnerabilities.
Just like Nextbank, GOMobile’s security has been rock solid, too.
In Closing: How To Secure Mobile Banking App
This article has covered how to secure mobile banking app with some actionable practices. These include authentication and authorization, machine learning, secure coding practices, encryption, and two-factor authentication or multi-factor authentication.
Also, note that cybercriminals aren’t taking a break, and neither should you. Stay vigilant and adapt to new threats as they emerge.
Finally, contact our banking app development company if you need help building a truly secure mobile banking app for your financial services. We’ll work together and develop effective security solutions without neglecting the customer experience.







