Fraud has become a multi-billion-dollar menace for most, if not all, businesses across various industries.
In 2024 alone, over $1.03 trillion was lost to different online scams globally. Unfortunately, despite online safety and security being a key concern for most consumers, only 67% of people globally feel confident in their ability to detect scams.
Therefore, it’s up to businesses to ensure their clients are safe by building a fraud detection system that spots and stops suspicious activities in real time without disrupting legitimate transactions.
In this article, we’ll dive deeper into how to build a fraud detection system that actually works. Discover what makes an integral part of a fraud detection pipeline and build protection mechanisms that make it almost impossible to commit fraud.
What are fraud detection systems?
Fraud detection systems are technology-driven solutions that identify, prevent, and mitigate fraudulent attacks.
They use a combination of AI, machine learning algorithms, behavioral analytics, and rule-based systems to flag suspicious transactions or activities and trigger appropriate actions.
Importance of fraud detection in modern business
Modern businesses can not ignore fraud detection systems due to the rapid digitization of financial transactions.
Currently, 73% of US consumers use mobile wallets, 81% have adopted retail apps, and more than eight out of ten shoppers rely on P2P payment apps.
That means you have no choice but to adopt these and other digital platforms to create seamless customer experiences that convert and retain your customers. An effective fraud detection system will help your modern business protect sensitive customer data on these platforms to enhance customer trust and retention.
Moreover, using AI and machine learning for fraud detection minimizes fraud attacks, which will help your business ensure regulatory compliance. This protects you from expensive legal fines, lawsuits, and other related financial losses.
Advanced AI and ML fraud detection systems will also lead to fewer false positives, helping you avoid reputational damage.
Common types of fraud in various industries
Whenever the word “fraud” is mentioned, most people immediately think of the banking or fintech industry. But, fraud is not limited to a single sector.
Here are some common fraud types across key industries:
- Finance and banking: Credit card fraud, identity theft, account takeover, and Authorised Push Payment (APP) fraud
- eCommerce: Chargeback fraud, transaction payment fraud, account takeovers, refund fraud
- Healthcare: Prescription drug fraud, medical identity fraud, medical billing fraud, and insurance fraud.
- Telecommunications: Subscription fraud, SIM card cloning
Key components of a fraud detection system
An effective fraud detection system combines multiple components to achieve high accuracy, minimal false positives, and rapid response times. The key components include:
Data collection and integration
Fraud detection begins with collecting and integrating data from multiple sources to create a comprehensive view of user behavior and transactions. The data is then consolidated into a single dataset, making it easy to identify anomalies.
Fortunately, there’s no shortage of customer data to collect and integrate since businesses handle lots of structured (transaction records) and unstructured data (email, support tickets).
For instance, a banking fraud detection system requires training data on card transactions, ATM withdrawals, login attempts, location, IP addresses, and user behavior analytics. You can source the data from mobile banking app logins, website visits, and even your call centers.
Real-time data ingestion and processing
Fraudsters act fast. They often execute fraudulent attacks within minutes. To counteract this, modern fraud detection systems rely on real time transaction data ingestion and processing. Otherwise, fraudulent transactions may go unnoticed until it’s too late, resulting in financial losses, data breaches, or regulatory penalties.
Businesses rely on high-speed stream processing frameworks such as Apache Kafka and Apache Flink to analyze transactions as they occur and detect anomalies in real time. These technologies allow fraud detection systems to interpret millions of events per second. This facilitates low-latency decision-making and ensures no suspicious activity goes unnoticed.
Analytical models and algorithms
Effective fraud detection relies heavily on the different systems and relative analytical algorithms that assess transaction patterns and identify suspicious activities.
- Machine learning systems: Uses supervised and unsupervised learning to detect anomalies and predict fraudulent behaviors.
- Supervised learning requires labeled historical data (fraud vs. non-fraud transactions). It uses algorithms like Random Forest and Logistic Regression to identify common fraud characteristics.
- Unsupervised learning is used when fraud labels are either unavailable or unknown. It uses algorithms like K-Means Clustering and Autoencoders. The algorithms detect anomalies and outliers in transaction behavior.
If, say, a customer who usually spends $500 per month suddenly makes a $10,000 purchase from another country, an anomaly detection model will flag it for review or assign a high fraud score.
- Rule-based detection systems: Uses predefined rules like flagging transactions over a certain amount or those originating from high-risk locations and detecting multiple failed login attempts in a short period.
Combining the analytical models with rule-based detection helps reduce false positives, improve fraud detection rates, and ensure accurate, real-time decision-making.
Alerting and response mechanisms
When an anomaly is first detected, the system generates an alert based on the risk level. These alerts are typically categorized into:
- Low-risk alerts: Activities that differ slightly from normal behavior but don’t strongly indicate fraud, such as a customer logging in from a new device.
- Medium-risk alerts: Suspicious activities that may require additional verification, such as a high-value transaction from an unusual location.
- High-risk alerts: Strong fraud indicators that require immediate action, such as multiple failed login attempts followed by a successful login from an unknown IP address.
The alerts are followed by relevant responses like blocking transactions, freezing accounts, or requesting two-factor authentication. Such responses triggered by data analytics stop any fraudulent activities before the transactions are completed.
Steps to develop a fraud detection system
Now, let’s explore step-by-step how to build a fraud detection system.
1. Define fraud scenarios and objectives
The first step in developing a fraud detection system is identifying the specific fraud scenarios relevant to your industry and business.
As mentioned earlier, fraud can take various forms, such as identity theft, account takeovers, payment fraud, or insider threats, and each requires a different detection setup. Having a clear definition of key fraud scenarios helps you determine the most ideal detection strategy.
Additionally, it’s crucial to set clear objectives for your fraud detection system. Well-defined fraud detection goals will ensure your system is aligned with business needs, customer expectations, and regulatory requirements.
Some of the goals you can set include reducing false positives, improving detection speed, or minimizing financial losses by X% within a specific timeframe (say six months or ten).
2. Collect and prepare relevant data
A fraud detection system is only as effective as the quality of the data it is trained on. A well-structured and comprehensive dataset will improve the system's ability to detect fraudulent patterns while minimizing false positives.
Therefore, the first step in this process is to collect data from various internal and external sources. Internal data sources include transaction records, user behavior logs, financial details, and account activity. On the other hand, external sources can be fraud intelligence feeds, industry blacklists, and third-party risk assessments.
Raw data often contains duplicates, errors, inconsistencies, and missing values that can impact fraud detection accuracy. So, clean your data before feeding it into analytical models to ensure you’re working with the most accurate and useful information.
For instance, if you’re in finance, you must remove duplicate entries, verify timestamps, and convert different currencies into a common base currency like USD.
You can implement feature engineering to ensure your data will actually help improve your predictions’ accuracy.
Feature engineering ensures that your data contributes to more accurate fraud detection predictions. It involves creating, transforming, and selecting meaningful features from raw data to enhance model performance. Examples of features can be transaction frequency, geolocation analysis, and transaction amounts.
3. Select appropriate analytical techniques
The next key step in building a fraud detection system is selecting the right analytical techniques. Fraudsters are constantly evolving their tactics. Your system needs to be fast, accurate, and adaptable to stay one step ahead. Here are some techniques you can use.
Rule-based systems
The approach uses predefined rules to flag suspicious activity based on known fraud patterns. For instance, you can set up rules like:
- Flagging credit card transactions over a certain amount (say purchases above $10,000)
- Blocking transactions from high-risk countries
- Detecting multiple failed login attempts
Rule-based detection is easy to implement and interpret. However, it struggles with evolving fraud tactics, meaning it might miss new fraud attacks entirely or generate many false positives. Nevertheless, it’s still a great starting point.
Anomaly detection
Fraud often involves unexpected or unusual behavior. With anomaly detection, your system learns what "normal" user behavior looks like and flags anything that deviates from this.
For example, if a customer who usually makes small purchases suddenly spends $5,000 in a foreign country, the system can identify this as a potential fraud attempt.
Machine learning and AI-based systems
As highlighted earlier, machine learning has two key categories: Supervised and unsupervised learning.
Supervised machine learning models, such as Logistic Regression, Gradient Boosting, and Random Forest, are trained on labeled fraud data. The model training allows them to easily recognize patterns in fraudulent transactions and classify new transactions as fraudulent or legitimate.
For example, in banking, you can train machine learning models to analyze millions of past transactions to help them identify current fraud activities based on common characteristics.
Unsupervised learning techniques, like autoencoders, clustering algorithms, and deep learning, detect hidden fraud patterns in large datasets without labeled fraud cases. These models work by detecting anomalies and outliers in transaction behavior, making them ideal for identifying or predicting new fraud tactics.
4. Implement real-time monitoring tools
Your fraud detection system should be proactive to ensure maximum impact. It must identify and stop fraud attempts before they get costly. This is why your business should adopt real-time monitoring tools.
To monitor transactions and activities in real time, your fraud detection system must collect, analyze, and respond to data instantly. The process usually starts with data streaming and collection from multiple sources, such as login attempts, IP addresses, payment details, and user behavior.
Tools like Apache Kafka, Flink, and Structured Streaming can help process this data as it comes in.
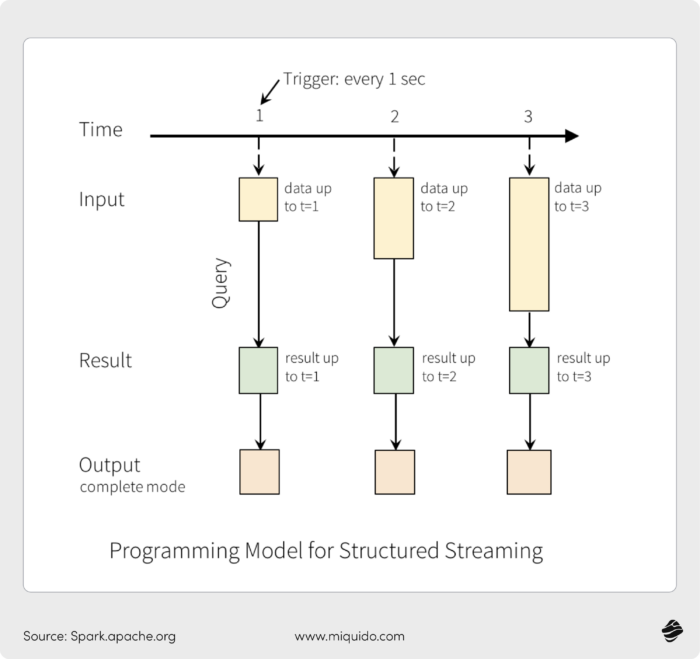
In addition, machine learning frameworks like TensorFlow and Scikit-learn can be used to get accurate fraud predictive analytics.
Once the data is collected, it will be analyzed using fraud scoring models to assess the likelihood of a transaction being fraudulent. These models assign a fraud score to each transaction, user action, or account based on multiple risk factors. The higher the score, the greater the probability that the activity is fraudulent.
5. Establish response protocols for detected fraud
Detecting fraud is only the first half of ensuring your business’s and users’ online security. The other half is how quickly and effectively you respond.
Structured response protocols help you act swiftly to prevent further damage and ensure compliance with legal and security standards.
So, what do you include in your response protocols?
First, always remember that not every suspicious activity flagged by your fraud detection system is actually fraud. False positives, which are legitimate transactions mistakenly marked as fraudulent, will only cause unnecessary delays that frustrate customers.
That’s why your first step should be to verify whether the detected activity is truly fraudulent. You can do that through quick biometric verification or multi-factor authentication (MFA).
For better security, use context-aware MFA, which assesses factors like location, device type, IP address, and access time. It also includes additional verification steps for high-risk situations.
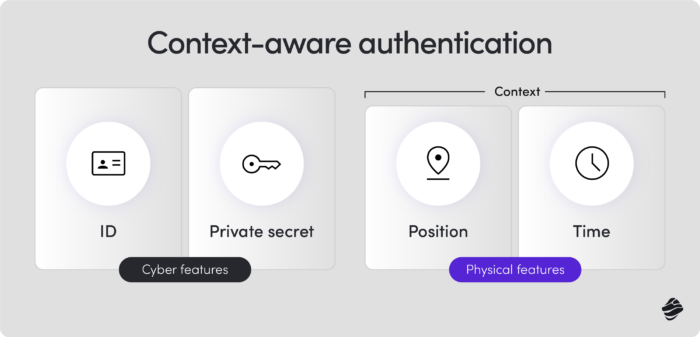
Next, clearly outline your response system. How will you react to different levels of fraud threats? Include both automated actions and manual interventions to ensure efficiency and accuracy. Automated actions include:
- Freezing suspicious accounts
- Declining high-risk transactions
- Triggering security protocols like enforcing password resets or locking accounts after multiple failed login attempts
Reserve manual interventions by your fraud response team for complex cases or situations that require deeper investigation.
The other item on your list should be how and when you communicate to customers whose accounts or transactions have been flagged for fraud. A poor fraud alert experience, like locking their account without explanation, will lead to frustration that will damage customer trust.
Instead, clearly explain the situation in simple, reassuring, non-technical language. Then, provide the steps for securing their account, such as changing passwords, verifying their identity, or contacting customer support.
Here’s a simple example.
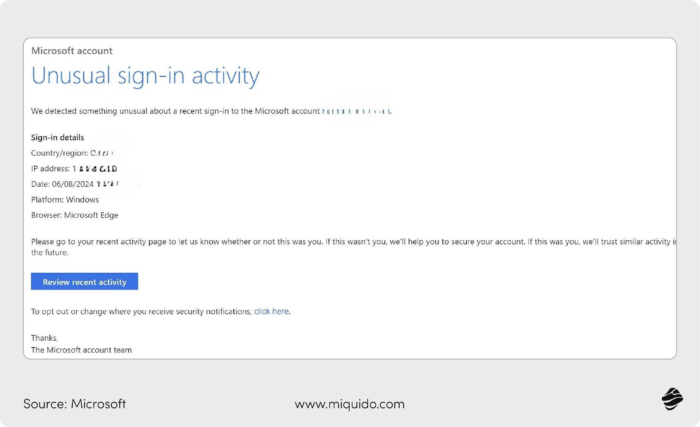
Also, use multi-channel notifications (SMS, email, push notifications) to ensure the customer gets the message as soon as possible.
Finally, depending on your industry, you may be legally required to report fraud to certain regulatory bodies or law enforcement. In the financial sector, you may need to report some fraud cases to law enforcement agencies, financial regulators, and credit bureaus. So, provide the guidelines on how to do it right in your fraud response protocols.
Fraud detection systems challenges and considerations
Like any other constantly evolving system, a fraud detection system comes with unique challenges and considerations.
Handling imbalanced datasets
In most industries, fraudulent transactions make up only a tiny fraction of overall transactions.
This imbalance can make it difficult for machine learning models to accurately identify fraud because they are mainly trained on legitimate transactions. The models don't learn the patterns and features that distinguish fraudulent transactions effectively, leading to many false negatives (missed fraud cases).
To avoid this, increase the number of instances in the minority class using techniques like Synthetic Minority Over-sampling Technique (SMOTE). SMOTE basically generates synthetic samples for the minority class. This means your model will learn from fraudulent and legitimate transactions equally, creating a balance in the dataset.
Also, don’t use traditional evaluation metrics, like accuracy, alone. Even a model that wrongly predicts all transactions as non-fraudulent can still achieve high accuracy due to the imbalanced datasets. So, embrace more comprehensive metrics like precision, recall, and F1 score.
Ensuring system scalability and performance
Fraud detection systems must handle large volumes of data, especially for banking, eCommerce, and healthcare software, since they process lots of transactional data.
If your system isn’t at peak performance or scalable, you will experience delays or totally missed fraud cases. This will lead to a loss of customer trust and, ultimately, high operational costs.
Use cloud-based infrastructure that can scale as transaction volumes grow to ensure system scalability and performance. Also, implement stream processing tools like Apache Kafka and Flink for timely detection and response.
Maintaining data privacy and compliance
Your fraud detection system will process sensitive information like financial details, login credentials, and IP addresses. If this data is not handled securely, it could be exposed to cyberattacks, which could also result in data breaches.
Data breaches harm your reputation and make it easier for cybercriminals to commit more fraud crimes using the stolen information. That’s why it’s imperative that you secure every data handling stage, from data collection to processing and storage.
To maintain data privacy:
- Only collect the data necessary for fraud detection
- Encrypt all sensitive data both in transit (when it's being sent) and at rest (when it's stored) to prevent unauthorized access.
- Hide personally identifiable information where possible. For instance, instead of storing full credit card numbers, use tokenization techniques.
- Restrict access to data using MFA and role-based permissions. This ensures that only authorized personnel handle sensitive information.
Depending on your industry and location, you may need to comply with various data protection laws and regulations, such as GDPR, CCPA, or PCI-DSS. Failure to comply can result in huge fines and legal consequences.
For example, GDPR violations can lead to fines of up to €20 million or 4% of annual global revenue.
Fraud detection systems examples
Let’s look at some real-world implementations of fraud detection systems.
Mastercard’s Decision Intelligence system
Decision Intelligence (DI) is an AI-driven fraud detection system from MasterCard that assesses the risk of every card transaction in real time. It helps banks and merchants detect fraud before it occurs.
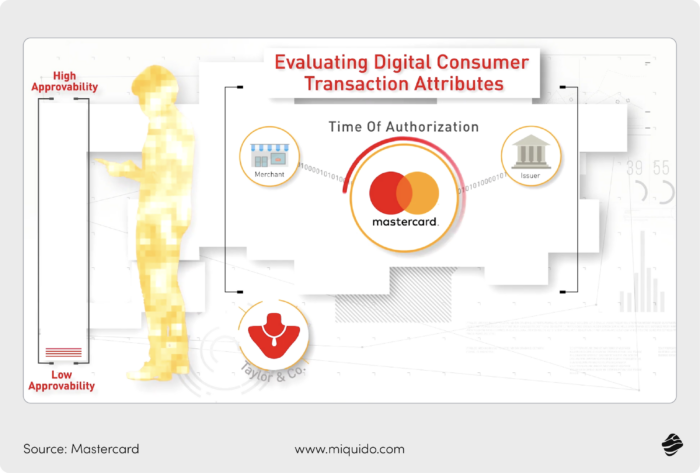
The system uses AI, Machine Learning techniques, and unique network insights to generate a transaction score and reason code that indicates the fraud risk attached to each transaction. This score allows users to spot risk trends and set relevant rules to help them make better decisions and approve genuine transactions.
Their latest enhancement, Decision Intelligence Pro, uses generative AI to scan around one trillion data points to predict whether a transaction is genuine or not. This significantly improves fraud detection rates and reduces false positives.
In addition, DI Pro can assess transactions in less than 50 milliseconds, which helps it provide quick and accurate fraud detection.
Lessons learned:
- Leveraging advanced AI and machine learning is crucial for improving the accuracy and efficiency of a fraud detection model
- The precision of your fraud detection solution can significantly increase accuracy and reduce false positives by over 85%.
J.P. Morgan’s Safetech Fraud solution
J.P. Morgan's Safetech Fraud and Card Testing Management solution is a fraud prevention tool that protects online merchants from card testing attacks.
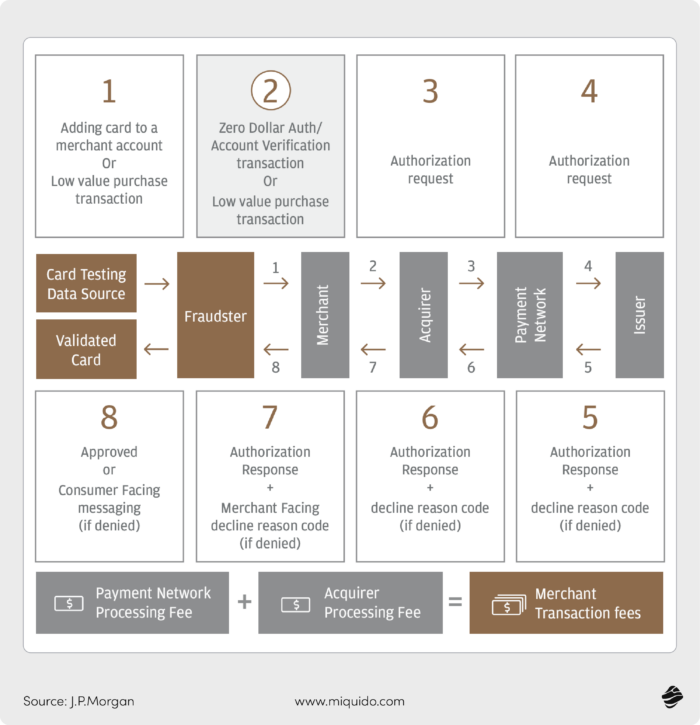
Safetech uses multiple layers of security measures, including device fingerprinting, proxy piercing, dynamic order linking, and dynamic risk scoring, to identify and block fraudulent activities.
The solution leverages its global network and adaptive AI algorithms to analyze transaction data accurately and in real time. It then generates a safety rating and other key data points, allowing users to assess trust level automatically.
If the trust level is low, the card authorization attempt is declined. If it’s high, the attempt is approved and sent to the issuing bank as an authorization request.
Lessons learned:
- Implementing multiple layers of security measures increases card fraud detection effectiveness.
- Monitoring transactions in real time will help you quickly identify and mitigate fraudulent activities.
- A global network provides a more comprehensive view of transactions, which can boost the accuracy of your fraud detection system.
Future trends in fraud detection
What are the trends shaping the future of online fraud detection? Well, here are two things to keep in mind:
1. Advances in Machine Learning and AI
AI and machine learning (ML) solutions are and will continue to be at the forefront of fraud prevention.
Advanced AI and ML algorithms have become even better at recognizing complex patterns or subtle anomalies in vast amounts of data that traditional systems might miss.
In addition, modern AI-driven systems can analyze transactions as they occur to help businesses detect and respond quickly to potential fraud.
Unlike rule-based systems that rely on predefined fraud patterns, AI-driven models adapt and learn from new fraud attempts. AI predictions show that the technology will become smarter and more secure. This guarantees that AI-powered fraud detection systems will be faster, more adaptive, and highly accurate.
2. Emerging technologies impacting fraud prevention
Blockchain development and advanced biometrics are other emerging technologies reshaping fraud prevention and detection.
Blockchain's decentralized nature prevents data tampering and enhances transparency in financial transactions. Fingerprint scanning, facial recognition, and behavioral biometrics add an extra layer of security for identity verification.
For instance, behavioral biometrics analyze how users interact with devices and systems, including how they type, their mouse movements, and their touchscreen gestures.
These behaviors are unique to each individual and are difficult for fraudsters to replicate. As such, they make it easy to detect fraud without compromising user experience.
Conclusion
With online transactions and digital app usage at an all-time high, businesses must actively protect their financial assets, prevent reputational damage, and maintain customer trust. One great way to achieve this is by creating advanced fraud detection systems.
The key components of an effective fraud detection system are data collection and integration, real-time data processing, analytical models, and response mechanisms. This article has also covered how to build a fraud detection system.
Your fraud detection system will, of course, face certain challenges like imbalanced datasets, data privacy and stringent regulations, and ensuring scalability and good performance. But despite these challenges, the future of fraud detection is promising.
Constant advancements in technologies like AI, machine learning, blockchain, and biometric authentication will continue to enhance fraud prevention. Fraud detection systems will definitely become quicker, more accurate, and more secure.

![[header] how to build a fraud detection system](https://www.miquido.com/wp-content/uploads/2025/02/header-how-to-build-a-fraud-detection-system.jpg)



![[header] top ai fintech companies transforming finance in 2025](https://www.miquido.com/wp-content/uploads/2025/05/header-top-ai-fintech-companies-transforming-finance-in-2025-432x288.jpg)
![[header] how to reduce churn on a form validation stage (1)](https://www.miquido.com/wp-content/uploads/2025/12/header-how-to-reduce-churn-on-a-form-validation-stage_-1-432x288.jpg)
